- Mint Media
- Posts
- The Bull Is Back And So Are Scams: A Degen Guide To Safety
The Bull Is Back And So Are Scams: A Degen Guide To Safety
Keep Your Winning Secure
Any views expressed in the below are the personal views of the author and should not form the basis for making investment decisions, nor be construed as a recommendation or advice to engage in investment transactions.
Gm everyone! Wilson here. Most of this was written a few days ago to be sent out this morning, but some updates made throughout in light of events earlier today. Enjoy!
Thought it was really important to bring back our good friend Beau (TheChild). For those who don’t know him, Beau is the Community Safety Lead at Pudgy Penguins and is an expert in all though security when it comes to web3.
As the markets continue to heat up going into 2024, scam attempts are expected in increase as well (they already have). While security isn’t always fun, it is the most important consideration when operating in this space. What’s the point of making internet money if you can’t keep it secure? Anyways, we’re super grateful that Beau was able to put this together for us. This is an amazing post, and I strongly recommend you take your time reading it. Have a great rest of your week, and stay safe out there!
The Ledger Connect Exploit
Holy shit what a day! As I was writing this article over the last couple weeks I had no idea the day we planned to publish it we’d see an extremely dangerous exploit impacting trusted sites like Sushi Swap, revoke.cash and more. Here’s the simple version of what happened:
Many websites use Ledger’s (yes the hardware wallet company) wallet connect kit to allow wallets of all shapes and sizes to connect to their site.
Scammers inserted malicious code and drainer contracts into this wallet connect kit, which placed them into the front end of trusted sites.
If you tried to use these sites this morning you may have been prompted with a malicious signatures, which some signed, resulting in some drains.
Ledger acknowledged the issue and is rolling out new code. Best to sit on your hands for a while as all the websites push out updates.
Bottom line here - always stay on your toes. Sometime’s its important to DO NOTHING while security companies respond and fix issues. Scam detector browser extensions that I’ll talk about below like Wallet Guard and Mint Defense would have caught this issue as the malicious signature popped up.
Now… on to the good stuff:
The Bull Market is BACK and scammers are coming for your freshly earned gains. Most people don’t give a shit about safety until something happens to them. Everyone assumes they’re good. It’s time to change that mentality before complex scams come back for real. As today shows, scams will come in all kinds of scary shapes and sizes. Having your fundamentals down pat will save you from most of these issues.
I’m Beau, the Community Safety Lead for Pudgy Penguins. I’m responsible for identifying new scams threatening our community and working with holders to develop sensible approaches to crypto safety and self custody. Huge thanks to Mint Media for letting me share a bit about safety. I regularly post about these issues, you can find me on X here. (LINK)
#1 NFT Scam of the Bear Market: Gasless Signatures to Steal NFTs with Open Wallet Approvals
More people were scammed during the bear by signing gasless signatures than any other method. If you sell NFTs on Opensea or BLUR you are vulnerable!
This scam takes advantage of your open approvals to marketplaces. When you sell an NFT on BLUR or Opensea you grant the Seaport contract permission to transfer all your NFTs from that collection. Scammers build websites that impersonate these marketplaces, or even specific collections and then write malicious smart contracts that use these existing approvals to list your NFTs for cheap/free. If you’ve accidentally navigated to a website impersonating an NFT project, it’s likely that the scammers have targeted their smart contract directly at that collection.
Here are a handful of easy things you can do to mitigate this threat.
Bookmark NFT marketplaces and DeFi websites. Only navigate to them from your bookmarks (never from email, X/Discord, or from any direct message conversation)
Don’t store NFTs on the same wallet you sell, claim, or trade from. We’ll talk about multiple wallets in a minute, but there is no need to place your long term holds at risk!
Use a Scam Detector or Transaction Simulator Service. These are typically browser extensions that look for malicious smart contracts and impersonator websites. They’ll give you a warning if you find something weird. They aren’t foolproof, but it is a good layer of security to add. The best are Wallet Guard (LINK), Pocket Universe (LINK), and Mint Defense (LINK).
Regularly clean up your open wallet approvals. If you don’t need to sell the NFTs on a wallet, use a tool like revoke.cash (LINK) to revoke Opensea or BLUR’s ability to access and transfer NFTs in your wallet.
Let’s Talk About Wallets
Use Multiple Wallets
Start using multiple wallets NOW. Many of you do this already for airdrop farming and keeping activity more anonymized, but it is critical for safety. This is the most important thing you can do to limit risk on the blockchain. Develop a system that works for you, but here’s mine:
You should have at least three wallets.
A Hot Wallet: Used for minting, airdrop farming, airdrop claims, and short term NFT flipping and coin trading. This wallet is for your riskiest on-chain activity -treat it as disposable and never leave more on it than you are willing to lose. This is your Metamask, Coinbase, or Phantom wallets and can be easily replaced. If you’re dedicated to mobile, I highly recommend checking out ZenGo - which is an MPC wallet and arguably much safer than other mobile wallets. (LINK)
A Lukewarm Hardware Wallet: Used for buying and selling expensive NFTs, larger token bags, or claiming NFT utility like airdrops, holder gated merch, and verifying in Discord. This wallet is “Lukewarm” because you’ll want to connect it (only using official connection methods) to your Metamask or other Hot Wallet but your seed phrase and private key is kept offline. NEVER import your Hardware wallet to a Hot Wallet with your private key or seed phrase.
A Cold Hardware Wallet: This is your “vault.” This wallet should be kept cold - meaning not connected to DeFi apps, NFT marketplaces, or online hot wallets. You should grant this wallet NO contract approvals (like giving Opensea permission to access NFTs or Uniswap access to a token). You will use the hardware wallet’s app like Ledger Live of Trezor Suite to send coins and NFTs to your selling wallet once you’re done holding them.
Using multiple wallets puts firewalls between your crypto assets. If one is compromised your risk is limited. You have to plan on you making mistakes. My system assumes that one day I will fuck up and get scammed or sign something malicious. If that happens, I won’t lose everything, only the handful of things “at risk” at any given time.
Hardware Wallets
Hardware wallets should be a key part of your safety strategy. Hardware wallets protect your seed phrase and private keys by keeping them offline and air-gapped from the computer you use for trading. If you accidentally download malware, your hot wallets will get drained as hackers will access your Private Keys. Hardware Wallets fix this.
The two leading Hardware wallet companies are Ledger (LINK) and Trezor (LINK). Ledger is probably easiest to use and supports more chains than Trezor, but following the Ledger Recover drama of this summer, some folks prefer Trezor. I personally use Ledger and have two separate devices so that I have separate seed phrases and private keys for each.
December 14 Update: The Ledger connect exploit this morning did not impact Ledger Hardware wallets. However, in my opinion Ledger has a severe trust deficit with crypto users and have some internal cleaning up to do. I’m going to be exploring Trezor more as an alternative to Ledger.
Wallet Delegation
Wallet Delegation emerged in earnest at the tail end of the last bull cycle. This allows you to “delegate” cold wallet permissions and NFTs stored in a cold wallet to a hot wallet. This enables the hot wallet to act on behalf of the cold wallet and is particularly useful for claiming utility or verifying ownership in a safe way.
The leading products in the space are called Delegate (LINK) and Warm (LINK). You can already use these products for things like Discord verification (Vulcan, CollabLand), Allowlists (Premint, Manifold), IRL Events (Tokenproof). Use Wallet Delegation everywhere that you possibly can. This is quickly becoming the industry standard and more and more teams are incorporating it into their products.
Seed Phrase Storage
There is no one-size fits all solution to seed phrase storage. You need to do what is right for you. Here are a few key points with seed phrase (or private key) storage.
Never store them digitally (in your notes app, a text message to yourself, or in a word doc or google doc). Malware will find this the second it hits your computer or your iCloud gets hacked.
Store your seed phrase in a place where you can access it easily, but strangers won’t be able to. This might be a locked drawer, safe, etc.
You can apply some light cryptography to your seed phrase to make it more secure if someone finds it. For example, you might want to switch word #3 and word #7 when you write it down, and only you will know the correct order of the words.
Let’s talk about avoiding scams
Updates in OTC trading
Over-the-Counter NFT trading was a hot spot for scammers last cycle. Throughout the bear, most platforms have taken steps to get rid of the exploits enabling these scams. Here’s what you need to know:
Reputable OTC platforms have removed trade links. If someone is sending you a link to SudoSwap, Opensea Deals, or another swap site it is a SCAM.
Some trade links have been replaced with trade IDs, but in general you will be able to find the proposed trade only by logging in to the site. There is no need to navigate to a trade offer from a DM someone sent you.
The best practice is to log into that site and check what offers you have received from there.
Ensure you bookmark reputable trading sites and use scam detector browser extensions.
Low Effort Scams Plaguing the Space
These scams are easy + cheap for scammers, but have a low success rate. You probably encounter these daily already, but it’s worth spelling them out.
Malicious Ads: Scammers buy ads on social platforms like X to promote malicious websites with drainer contracts
How it works: Pretty self explanatory, but X has made ads more difficult to distinguish from the timeline so you have to keep a close eye out for the “ad” designator in the top right corner of posts. If you click the ad and head to the site, you’ll quickly encounter a malicious contract hoping to drain your wallet! The X ads are typically related to an NFT or crypto claim or mint and span both NFT/crypto IPs or Web2 ones with hooks like “claim Disney’s first NFT!”
What it looks like:

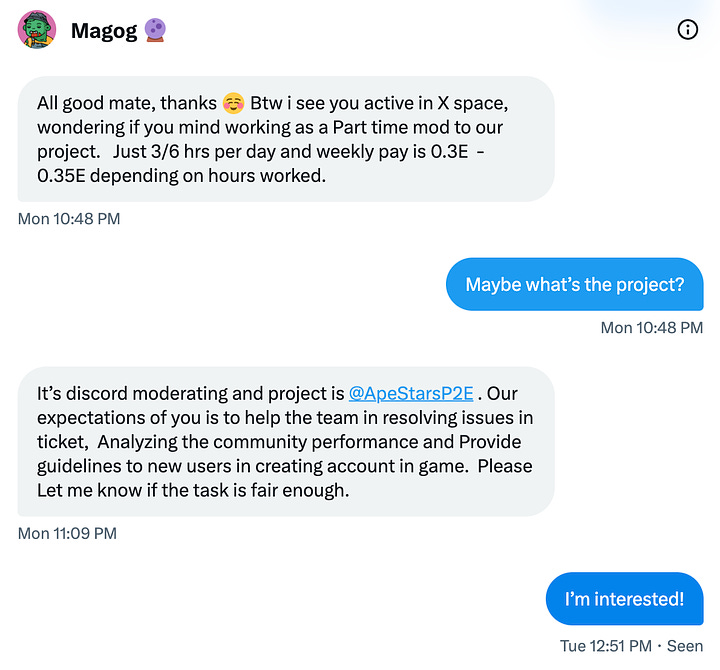
Game Beta Tester/Moderator/Ambassador Job Offer: Scammers offer job opportunities as a game beta tester, moderator, ambassador, or other similar job in order to get you to download malware or sign a malicious tx
How it works: You receive a DM from a “community manager” for a new Web3 gaming company with an offer to become a beta tester or moderator for their game. They’ll pitch you and then direct you to a website where they’ll instruct you to follow the directions to download the game, which is actually malware. The malware will steal private keys related to any hot wallets on that device and will also search for seed phrase or private keys stored on your PC. A slight variation is to direct you to discord to receive a file to download the game or sign a malicious contract that appears like Collabland or another wallet verification system
What it looks like:

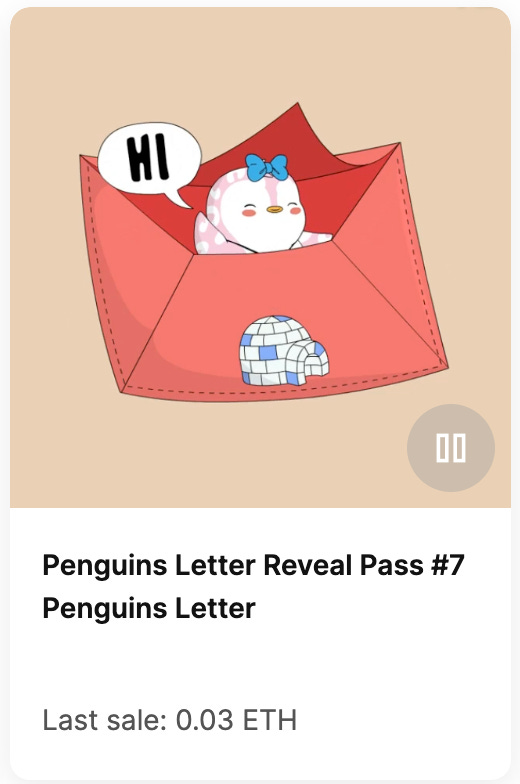
Airdropped NFTs: Scammers Airdrop NFTs impersonating popular projects or IPs hoping to distribute malicious websites
How it works: You check your wallet and notice a brand new NFT with your favorite project’s brand and logo on it. It has a WETH offer on it so you think you’ve just received free $. You click on the collection or NFT to learn more and there is a link to a website in the description, often with a call to action like “reveal your NFT” or “there’s still time to mint”! That website will have a malicious smart contract that will steal your coins if you sign.
What it looks like:

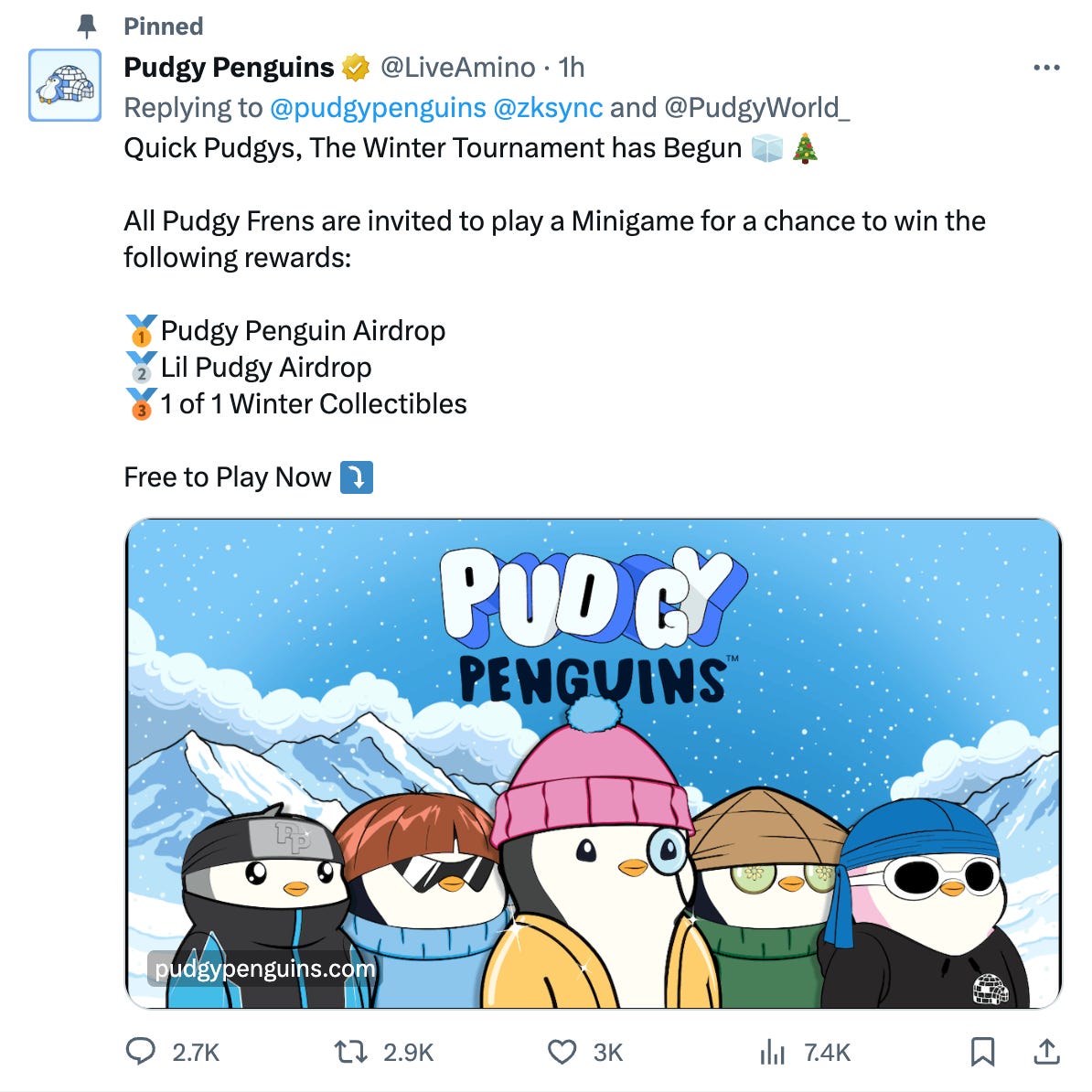
Impersonator Accounts: Scammers impersonate official accounts related to top NFT collections such as the CEO or Company account in order to distribute malicious websites
How it works: Scammers create an account and bot fake followers. When the real account they are impersonating posts on X, they reply to their tweet as if it is another post in a thread. This tweet typically contains a link to a malicious website containing wallet drainers. Occasionally these accounts also spread through mass tags. If someone tags you in something, ignore it!
What it looks like:
This section boils down to avoiding DMs. Set your DMs on Discord to friends only and be very wary of any DMs on X or other platforms. Assume every stranger in your DMs wants to scam you and sometimes your friends (or their impersonators will).
Sim Swaps and Account Takeover: Scammers often attempt to take over a real account to widely spread malicious websites and scams. These are the most dangerous
Personalized Job, Investment, or Advisory Offers: Unlike the beta tester/mod type roles mentioned earlier, these are elaborate and long scams focused on earning trust. They are personal and often the scammer targets specific victims based on how they invest, their job experience, and other factors like what NFTs or crypto you own. This can be weeks or months long. The delivery method of the scam could be a few different things, but will likely end up being malware or some type of malicious signature. The key here is doing due diligence and carefully researching any potential opportunity. Don’t ever sign anything for a job with a wallet containing expensive NFTs, there should be no need for it.
Various Social Engineering Scams: There are a variety of other SE scams to look out for. Usually these approaches start in DMs or through a random tag on X. The scammer may offer to get you on a whitelist, or animate your NFT, or claim some type of unique utility only available to people with your NFT holdings.
Safety Training
This article covers the basics, but safety is something worth really learning about. The Boring Security DAO has free classes that are perfect for NFT and crypto degens of all experience levels. If this struck a chord with you, take the time to take these courses and really get on top of your game.
Conclusion
Most people don’t give a shit about safety until something happens to them. Don’t let that be you. If you have questions or need help you can find me on X or in the Mint Media discord. It’s never a bother, let’s keep your cartoon animals safe!